 重要提示:
请勿将账号共享给其他人使用,违者账号将被封禁!
重要提示:
请勿将账号共享给其他人使用,违者账号将被封禁!
 题目内容
(请给出正确答案)
题目内容
(请给出正确答案)
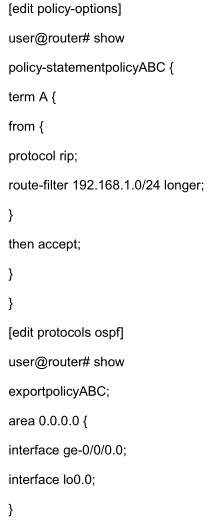
A. The route 192.168.1.0/25 is accepted
B. The route 192.168.2.0/24 is accepted
C. OSPF routes will be exported into RIP
D. RIP routes will be exported into OSPF
 更多“Referring to the exhibit, which two statements are true?()”相关的问题
更多“Referring to the exhibit, which two statements are true?()”相关的问题
第1题
e firewall enforcer. The MAG Series device resides in the same security zone as users. However, the users reside in different subnets and use the SRX Series device as an IP gateway.Which statement is true?()
A. You must configure a security policy on the SRX Series device to allow traffic to flow from the user devices to the MAG Series device.
B. No security policy is necessary on the SRX Series device to allow traffic to flow from the user devices to the MAG Series device.
C. You must configure host-inbound traffic on the SRX Series device to allow SSL traffic between the MAG Series device and the user devices.
D. You must configure host-inbound traffic on the SRX Series device to allow EAP traffic between the MAG Series device and the user devices.
第2题
A. Chassis clusters are used to aggregate routes.
B. Chassis clusters are used to create aggregate interfaces.
C. Chassis clusters are used to group two chassis into one logical chassis.
D. Chassis clusters are used to group all interfaces into one cluster interface.
第3题
A. Odyssey Access Client
B. Junos Pulse
C. Java agent
D. Agent less access
第4题
A. The valid cluster-id range is between 0 and 255.
B. Junos OS security devices can belong to more than one cluster if cluster virtualization is enabled.
C. If the cluster-id value is set to 0 on a Junos security device, the device will not participate in the cluster.
D. A reboot is required if the cluster-id or node value is changed.
E. Junos OS security devices can belong to one cluster only.
第5题
00 minutes and the default Juniper Networks logo on the user interface page. The second role has a maximum timeout value of 1200 minutes and a custom logo on the user interface page.Based on the merging of these two roles, which two will be applied?()
A. A custom logo on the user interface page
B. A maximum timeout value of 600 minutes
C. A maximum time out value of 1200 minutes
D. A default Juniper Networks logo on the user interface page
第6题

A. to protect the Routing Engine
B. to protect all interfaces on the device
C. to protect the Packet Forwarding Engine
D. to protect the management interface
第7题
zonecalledUNTRUSTtotheaddressbookentryServerinazonecalledTRUST.However,theadministratordoesnotwanttheservertobeabletoinitiateanytypeoftrafficfromtheTRUSTzonetotheUNTRUSTzone.Whichconfigurationwouldcorrectlyaccomplishthistask?()

A.A
B.B
C.C
D.D
第8题
ss, any destination-address, and any application. The policy will be a source IP policy for use with the Junos Pulse Access Control Service.What must you add to complete the security policy configuration?()
A. The intranet-auth authentication option
B. The redirect-portal application service
C. The uac-policy application service
D. The ipsec-vpn tunnel
第9题
ry the10net in a zone called UNTRUST to the address book entry Server in a zone called TRUST.However, the administrator does not want the server to be able to initiate any type of traffic from the TRUST zone to the UNTRUST zone.Which configuration statement would correctly accomplish this task?()
A. from-zone UNTRUST to-zone TRUST { policy DenyServer { match { source-address any; destination-address any; application any; } then { deny; } } } from-zone TRUST to-zone UNTRUST { policy AllowTelnetin { match { source-address the10net; destination-address Server; application junos-telnet; } then { permit; } } }
B. from-zone TRUST to-zone UNTRUST { policy DenyServer { match { source-address Server; destination-address any; application any; } then {deny; } } } from-zone UNTRUST to-zone TRUST { policy AllowTelnetin { match { source-address the10net; destination-address Server; application junos-telnet; } then { permit; } } }
C. from-zone UNTRUST to-zone TRUST { policy AllowTelnetin { match { source-address the10net; destination-address Server; application junos-ftp; } then { permit; } } }
D. from-zone TRUST to-zone UNTRUST { policy DenyServer { match { source-address Server; destination-address any; application any; } then { permit; } } } from-zone UNTRUST to-zone TRUST { policy AllowTelnetin { match {source-address the10net; destination-address Server; application junos-telnet; } then { permit; } } }
第10题
A. The ability to detect and prevent malicious traffic.
B. The ability to associate security breaches with a specific user.
C. Converged management of network and security events, network flow data, and identity information.
D. Consistent device management across administrative realms.

 警告:系统检测到您的账号存在安全风险
警告:系统检测到您的账号存在安全风险
为了保护您的账号安全,请在“上学吧”公众号进行验证,点击“官网服务”-“账号验证”后输入验证码“”完成验证,验证成功后方可继续查看答案!
